Secure Protocols for Low Power Fitness Trackers
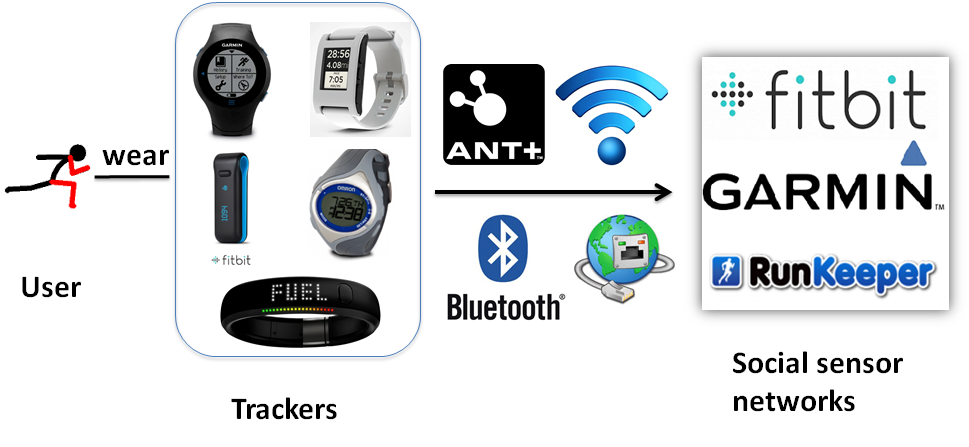
Wearable personal trackers that collect sensor data about the wearer, have long been used for patient monitoring in healthcare. Holter Monitors, with large and heavy enclosures, that use tapes for recording, have recently evolved into affordable personal fitness trackers. Recently, popular health centric social sensor networks have emerged. Products like Fitbit, Garmin Forerunner and Jawbone Up require users to carry wireless trackers that continuously record a wide range of fitness and health parameters (e.g., steps count, heart rate, sleep conditions), tagged with temporal and spatial coordinates. Trackers report recorded data to a providing server, through a specialized wireless base, that connects to the user’s personal computer. The services that support these trackers enable users to analyze their fitness trends with maps and charts, and share them with friends in their social networks.
 We demonstrate vulnerabilities in the storage and transmission of personal
fitness data in popular trackers from Fitbit and Garmin. We have built two
attack tools, FitBite and GarMax, and show how they inspect and inject data
into nearby Fitbit Ultra and Garmin Forerunner trackers. The attacks are fast,
thus practical even during brief encounters. We believe that, the
vulnerabilities that we identified in the security of Fitbit and Garmin are due
to the many constraints faced by solution providers, including time to release,
cost of hardware, battery life, features, mobility, usability, and utility to
end user. Unfortunately, such a constrained design process often puts security
in the back seat.
We demonstrate vulnerabilities in the storage and transmission of personal
fitness data in popular trackers from Fitbit and Garmin. We have built two
attack tools, FitBite and GarMax, and show how they inspect and inject data
into nearby Fitbit Ultra and Garmin Forerunner trackers. The attacks are fast,
thus practical even during brief encounters. We believe that, the
vulnerabilities that we identified in the security of Fitbit and Garmin are due
to the many constraints faced by solution providers, including time to release,
cost of hardware, battery life, features, mobility, usability, and utility to
end user. Unfortunately, such a constrained design process often puts security
in the back seat.
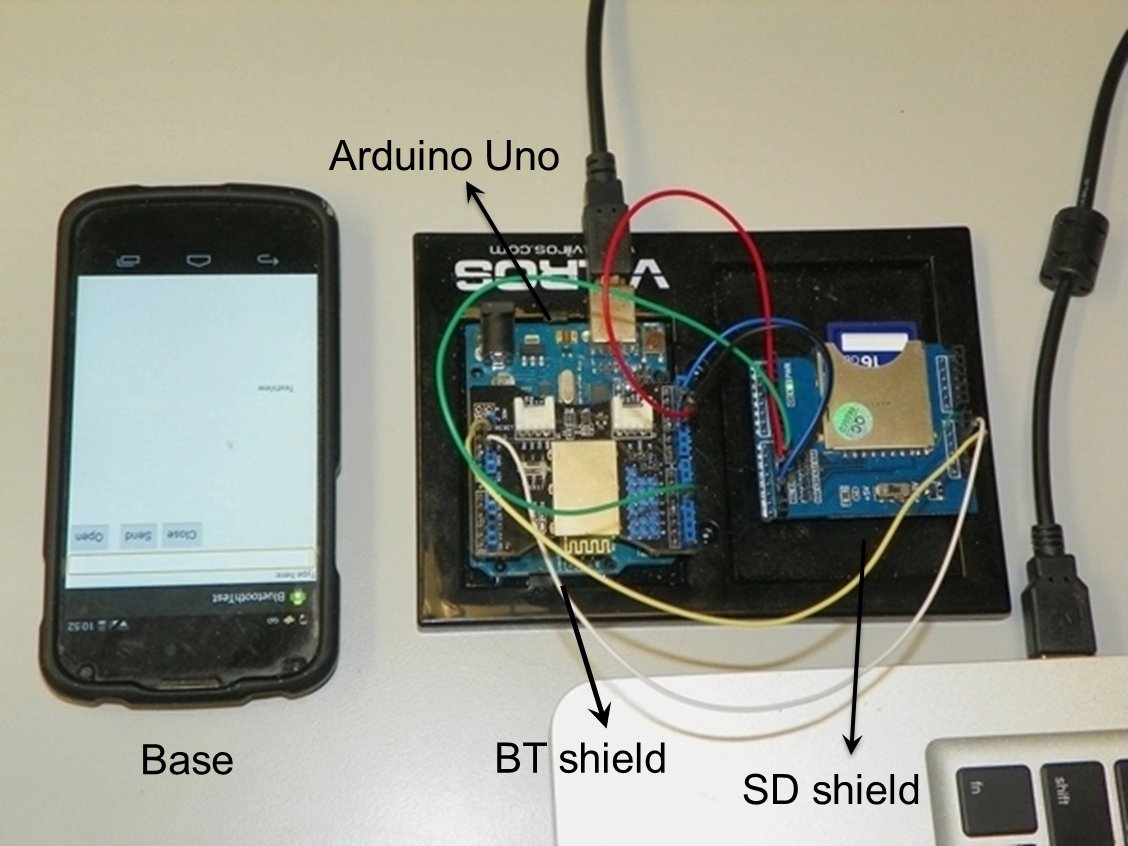 To help address these constraints, we study protocols for secure fitness data
storage and transmission on lightweight personal trackers. We leverage the
unique system model of social sensor networks to encode data stored on trackers
using two pseudo-random values, one generated on the tracker and one on the
providing server. This enables us to protect not only against inspect and
inject attacks, but also against attackers that physically capture and read the
memory of trackers. The hardware and computation requirements are
minimal, just enough to perform low-cost symmetric key encryption and
cryptographic hashes. We do not impose storage overhead on trackers
and ensures an even wear of the tracker storage, extending the life of flash
memories with limited program/erase cycles. We have developed Sens.io, a $52
tracker platform built on Arduino Uno, of similar capabilities with current
solutions.
To help address these constraints, we study protocols for secure fitness data
storage and transmission on lightweight personal trackers. We leverage the
unique system model of social sensor networks to encode data stored on trackers
using two pseudo-random values, one generated on the tracker and one on the
providing server. This enables us to protect not only against inspect and
inject attacks, but also against attackers that physically capture and read the
memory of trackers. The hardware and computation requirements are
minimal, just enough to perform low-cost symmetric key encryption and
cryptographic hashes. We do not impose storage overhead on trackers
and ensures an even wear of the tracker storage, extending the life of flash
memories with limited program/erase cycles. We have developed Sens.io, a $52
tracker platform built on Arduino Uno, of similar capabilities with current
solutions.
People
- Students
- Mahmudur Rahman: FIU
- Faculty
- Bogdan Carbunar: FIU
- Umut Topkara: IBM Research
Source Code
Please contact us to negotiate the release of our attack tools, FitBite and GarMax. We do this in order to ensure an academic use of the tools and prevent their distribution and use for malicious purposes.
Publications
Mahmudur Rahman, Bogdan Carbunar, Umut Topkara.
Accepted in the 22nd IEEE International Conference on Network Protocols (ICNP), [acceptance rate=18.99\%], Raleigh, North Carolina, October 2014. [pdf]
Media Coverage
- Paul Roberts. The Security Ledger. "Fitbitten: Researchers Exploit Health Monitor To Earn Workout Rewards"
- Amanda Alvarez. GigaOM. "Keeping Fitbit safe from hackers and cheaters with FitLock"
- Kathleen Comte. L'Atelier. "Les systemes de partage de donnees d'auto-mesure doivent-ils etre plus securises ?"
- Rachel Reilly. Daily Mail. "The tiny gadget that turns your fridge off when you eat too much"
- Robert Vamosi. Mocana. "FitBit Health Monitors Hacked"
